Here's how hackers hack using the ZANTI Application
To prevent ancman hacking you need to know how hackers work (doing the action).
Thus you can anticipate hacker attacks.
Actually the way hackers hack using zantis application is not much different from DSploit.
For the same preventive measures.
if you want to know more you can see my previous post about hacker action using DSploit and how to prevent it.
Follow us on telegramhttp://t.me/itscybertechI'd - @itscybertech

Aplikazi zantI is very easy to use, the hacker only requires root access on the smartphone.
This is one of the easiest hacking techniques, as for some other techniques, such as:
- Camouflage
- Sesion hijacking
- Dos attack
- Covering tracks
- Carding ect.
All of these techniques work flawlessly if you use a hacking operating system to support hacking activities.
Here's how hackers hack using the ZANTI Application:

After hackers equip smartphonnya with zanti application then hackers are ready to launch an attack.
Hackers can use this application to hack facebook account, Gmail, M Banking and many more.
Here's an example of an attack done by a hacker using zANTI:
Please Download zantis apk ↓
Before you use the application zANTI, your android smartphone must be in the root, if not please Root your Android first.
Step 1: open the Zanti app and Scan the entire wifi network.
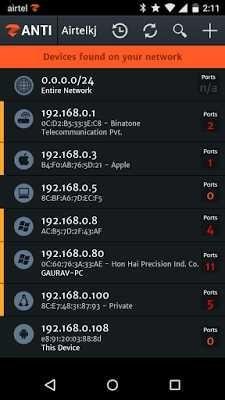
Hackers can see the devices connected to the wifi.
This zANTI application can also scan all ports as you see in the image above.
Select Ip whose port is open
Example: 192.168.0.100 (Mac OSX)
Step 2: After Opening the selected Ipkorban, the hacker can see the open port and some other details as shown in the picture below:
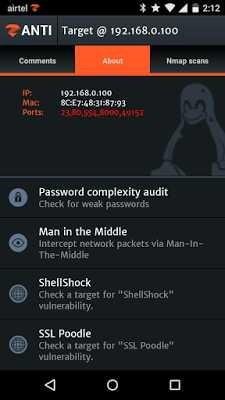
As you can see in the picture above, zANTI.apk successfully scans all hosts in the network and its potential victim settings.
In the Attack section:
- Audit Complexity Password: for password checks and violence ex: default password on victim.
- MITM: It intercept network packets through MITM.
- SHELLSHOCK attack: its vulnerability check is on the victim or not.
- SSL Poodle: to build SSL Poodle attacks or not.
It also shows Nmap Scan Results (Check image below)
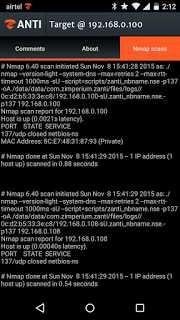
In this demo I used MITM Attack on Target.
Step 3: After Selecting MITM attack (Man In The Midle) hackers will see many things that hackers can do on target ex:
look at the picture below. To get your username and password using Zanti,
- click view on the Requests loger
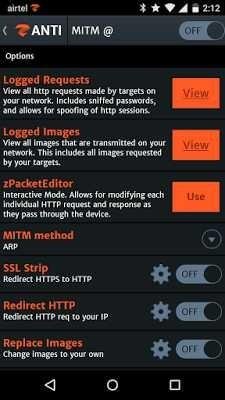
As you can see all the attacks that a hacker can do on a target by using MITM, by:
http://t.me/itscybertech
http://t.me/itscybertech
- Activate MITM slide to "ON" MITM on top right of it. * After that enable SSL Strip scroll "ON" SSL Strip. (Check picture below)
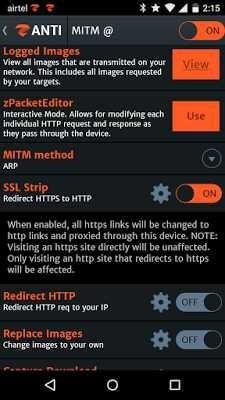
As you can see I selected "ON" both things together by using zantI..apk to hack passwords that are connected in one wifi network in MITM attacks from my android device to another phone hack or PC.
Continue:
Step 4: After that I sniff the package (Check picture below) and SSL Striping works perfectly and hotmail strip in HTTP.
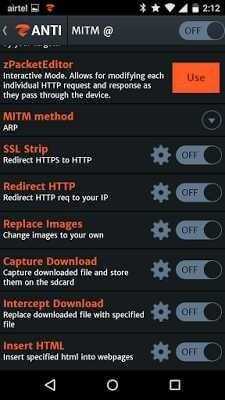
As you can see hotmail is a strip to http and ready to grab the password as soon as the victim enters the login details.
Pelu you know if you do not do login activity then hacker will not get username and password.
Now just visit (sesion hijacking) "http: // ....?" The korba visit and enter the username and password that is in the gap earlier.
Easy is not a Hack Username and Password Tutorial Using ZANTI Application on Android Which Is In One Wifi Network.
ZANTIi application can also transfer the victim to http ..? What has been specified by hackers.
Here is an example of the menu function zANTI.apk:
Reddirect HTTP, redirects the victim to http: // ....? .Replace Image, sends the image to the victim's visited web page.
Conclusion:
If you do not want your activities hacked by hackers, then as much as possible do not use free wifi hospot.
But if kepepet, try not to do activist login,
Especially entering into paypal account, Mbanking, it is very dangerous.
Can-can balance your savings in drain out.
This attack is commonly referred to as Sesion Hijacking.
This article I wrote for the purpose of prevention to avoid hacker attacks.
If there is any abuse related to the contents of this article, I am not responsible.
Once you know how to hack hack using ZANTI Application, you can be more vigilant.



Good buddy
ReplyDelete